Windows Admin Center : Install2024/12/26 |
|
Install Windows Admin Center.
It's possible to Manage Windows Server Hosts and Client Hosts on it. ⇒ https://docs.microsoft.com/en-us/windows-server/manage/windows-admin-center/understand/what-is If you manage only a Windows Host with Windows Admin Center, it's OK to install Admin Center on it, but if you'd like to manage multiple Windows Hosts, it needs to install Admin Center on a Gateway Server. The Windows OS that you can install Admin Center with Gateway Mode are Windows Server 2016 or later. By the way, Installing Admin Center on Domain Controller Hosts is not supported, so you need to choose to install Admin Cenetr as Gateway Server except DC. Anyway, Windows Admin Center does not require Domain Environmrnt, also possible to manage standalone Host on it. |
| [1] | To use with Windows Admin Center, obtain a valid SSL/TLS certificate like Let's Encrypt or others, or create a self-signed certificate. If you want to create a self-signed certificate, run like follows. If you use a valid certificate, you can skip follows. |
Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. # create with a validity period of 10 years PS C:\Users\Administrator> New-SelfSignedCertificate ` -DnsName "rx-7.srv.world" ` -KeyAlgorithm "ECDSA_nistP384" ` -KeyExportPolicy "Exportable" ` -CertStoreLocation "Cert:\LocalMachine\My" ` -NotAfter (Get-Date).AddYears(10) PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\My Thumbprint Subject ---------- ------- 60550BD40723E74D1711D007523A5A243A4E20A6 CN=rx-7.srv.world |
| [2] | Change the access permission of the private key of the SSL/TLS certificate so that it can be used with Windows Admin Center. Whether you use valid certificate or a self-signed certificate, set the following. |
Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. PS C:\Users\Administrator> Get-ChildItem Cert:\LocalMachine\My PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\My Thumbprint Subject ---------- ------- 60550BD40723E74D1711D007523A5A243A4E20A6 CN=rx-7.srv.world PS C:\Users\Administrator> $ObjCert = Get-ChildItem Cert:\LocalMachine\My\60550BD40723E74D1711D007523A5A243A4E20A6 PS C:\Users\Administrator> $Cert = [System.Security.Cryptography.X509Certificates.ECDsaCertificateExtensions]::GetECDsaPrivateKey($ObjCert) PS C:\Users\Administrator> $fileName = $Cert.key.UniqueName PS C:\Users\Administrator> $filePath = "$env:ALLUSERSPROFILE\Microsoft\Crypto\Keys\$fileName" # add [Full Control] perm to [NETWORK SERVICE] PS C:\Users\Administrator> icacls $filePath /grant "NT AUTHORITY\NETWORK SERVICE:(F)" processed file: C:\ProgramData\Microsoft\Crypto\Keys\43be1f13c85f82a6902b57e2a4e11c36_c75e32de-e145-41e1-b23c-02ec62c96380 Successfully processed 1 files; Failed processing 0 files # add [Read] perm to [Users] PS C:\Users\Administrator> icacls $filePath /grant "BUILTIN\Users:(R)" processed file: C:\ProgramData\Microsoft\Crypto\Keys\43be1f13c85f82a6902b57e2a4e11c36_c75e32de-e145-41e1-b23c-02ec62c96380 Successfully processed 1 files; Failed processing 0 files PS C:\Users\Administrator> icacls $filePath C:\ProgramData\Microsoft\Crypto\Keys\43be1f13c85f82a6902b57e2a4e11c36_c75e32de-e145-41e1-b23c-02ec62c96380 BUILTIN\Users:(R) NT AUTHORITY\NETWORK SERVICE:(F) BUILTIN\Administrators:(F) NT AUTHORITY\SYSTEM:(F) Successfully processed 1 files; Failed processing 0 files |
| [3] | If you created a self-signed certificate, add it to the trusted store. If you use valid certificate, you can skip the following. |
Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. PS C:\Users\Administrator> $ObjCert = Get-ChildItem Cert:\LocalMachine\My\60550BD40723E74D1711D007523A5A243A4E20A6 PS C:\Users\Administrator> Export-Certificate -Cert $ObjCert -FilePath "C:\Users\Administrator\rx-7.srv.world.cer" Directory: C:\Users\Administrator Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 12/25/2024 5:03 PM 476 rx-7.srv.world.cer PS C:\Users\Administrator> Import-Certificate -FilePath "C:\Users\Administrator\rx-7.srv.world.cer" -CertStoreLocation "Cert:\LocalMachine\Root" PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\Root Thumbprint Subject ---------- ------- 60550BD40723E74D1711D007523A5A243A4E20A6 CN=rx-7.srv.world |
| [4] |
Download the Windows Admin Center installer from the official website below. ⇒ https://www.microsoft.com/en-us/evalcenter/download-windows-admin-centerAfter downloading, run the installer and the following screen will appear. Click [Next] to proceed. |

|
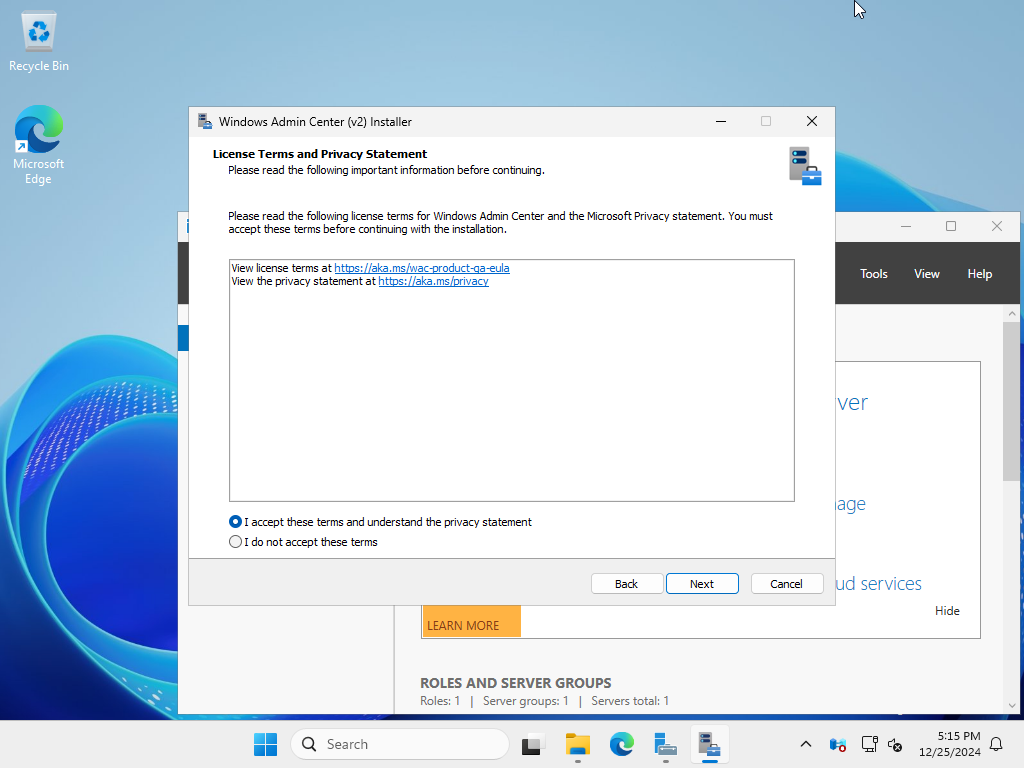
| [5] | Check the box to accept the terms of use and proceed to next step. |
|
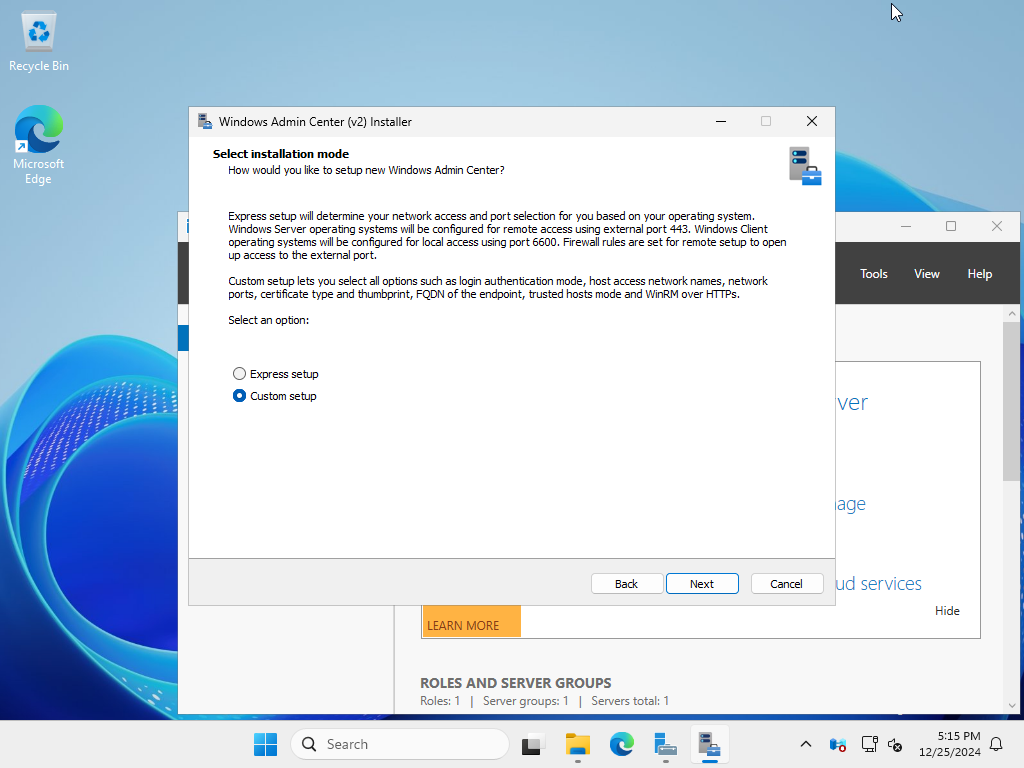
| [6] | Select [Custom setup] to specify the certificates you have obtained or created. |
|
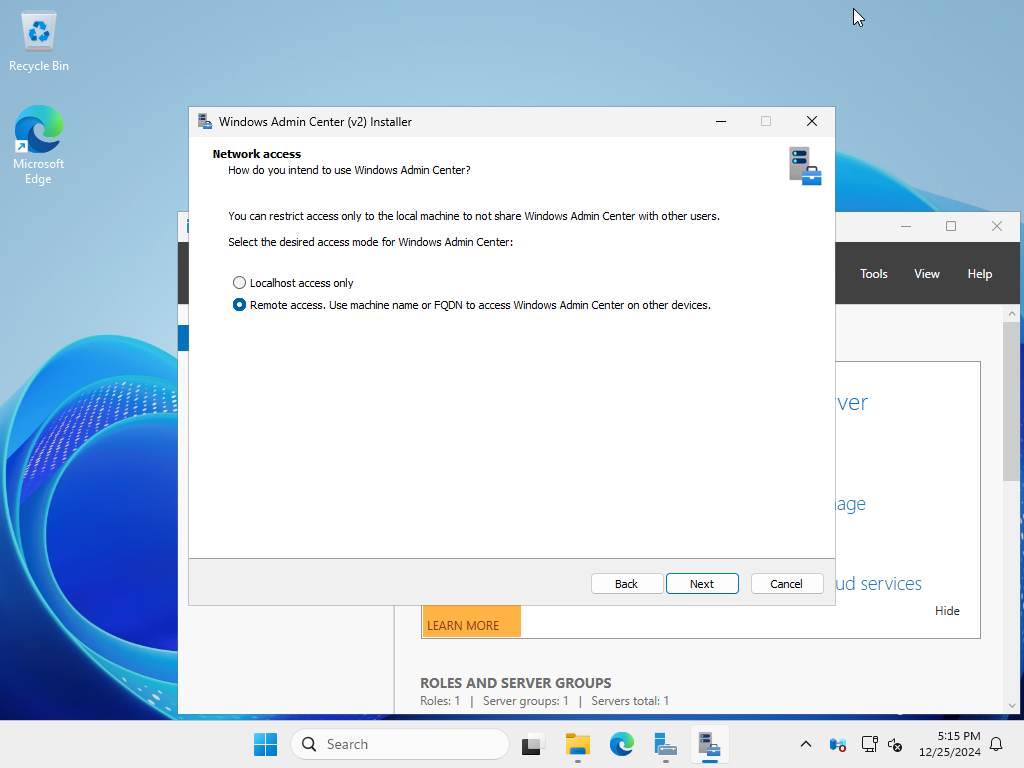
| [7] | Select whether to allow access to Windows Admin Center only from the local host or from other computers. In this example, we will leave it as the default (remote access allowed). |
|
| [8] | Select whether to use an HTML form or Windows authentication to log in to Windows Admin Center. In this example, we will proceed with the default (HTML form). |

|
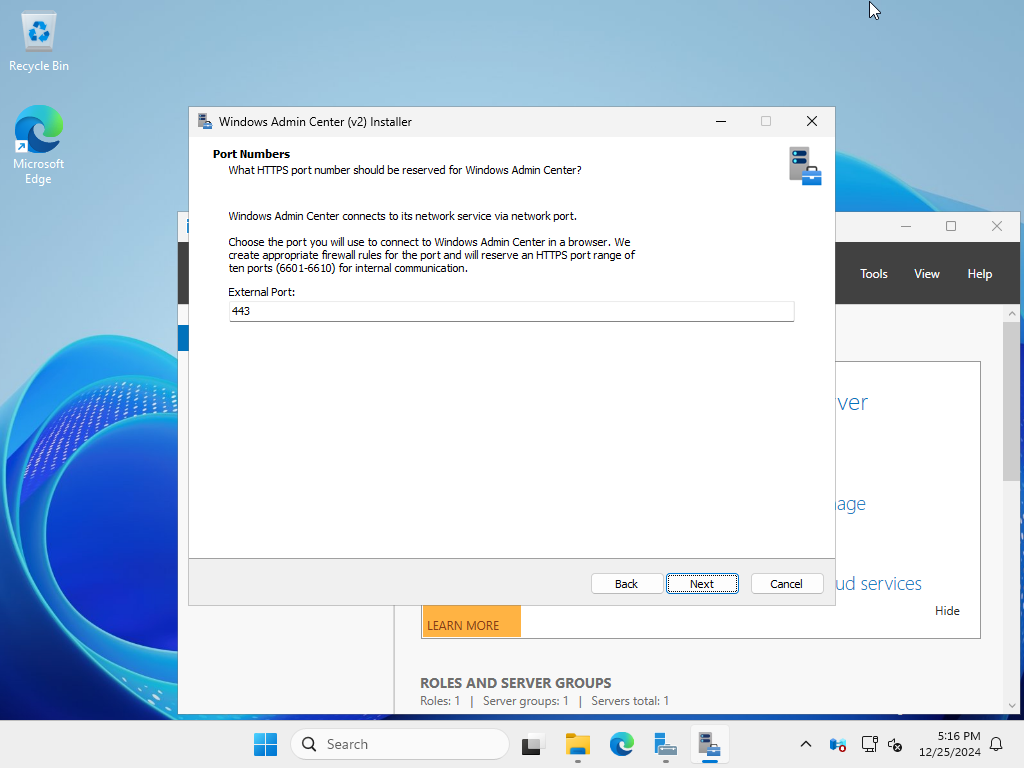
| [9] | Specify the port on which Windows Admin Center listens. In this example, we will leave it at the default (443). |
|
| [10] | Select the top option [Use the pre-installed TLS certificate], to specify the TLS certificate you obtained or created. The bottom option means that if you want the installer to generate and apply a self-signed certificate. The certificate generated by the installer has a short validity period of 60 days, so if you use a self-signed certificate, it is better to use a certificate you created yourself with a longer validity period. |
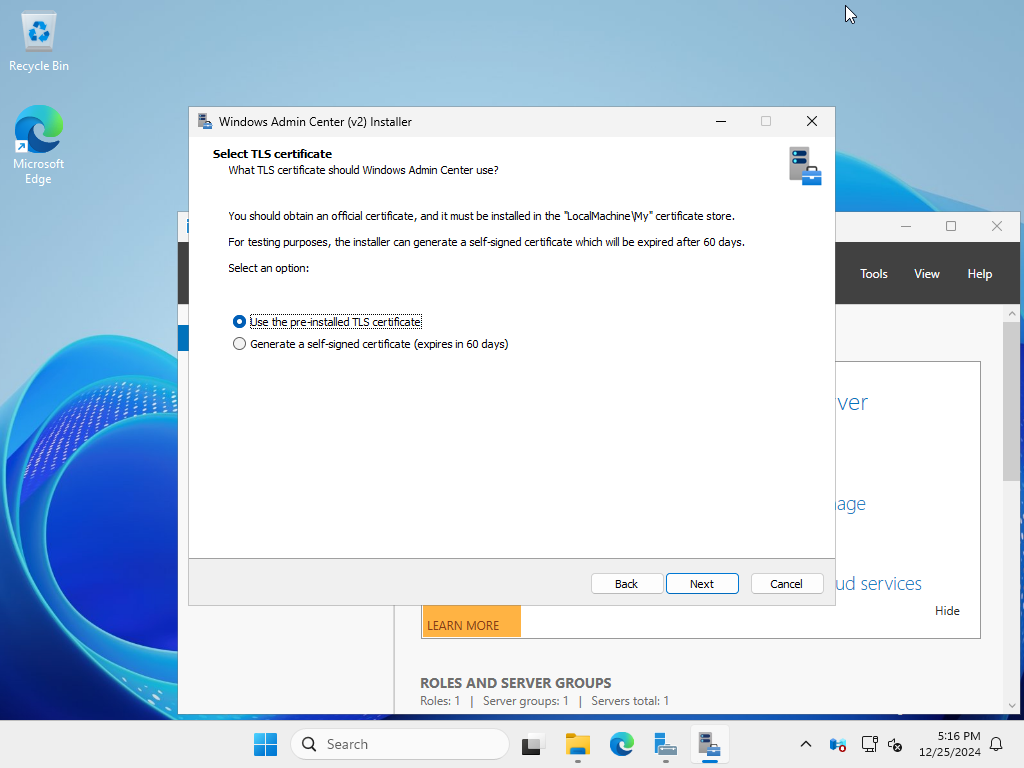
|
| [11] | Specify the thumbprint of the TLS certificate you obtained or created. |
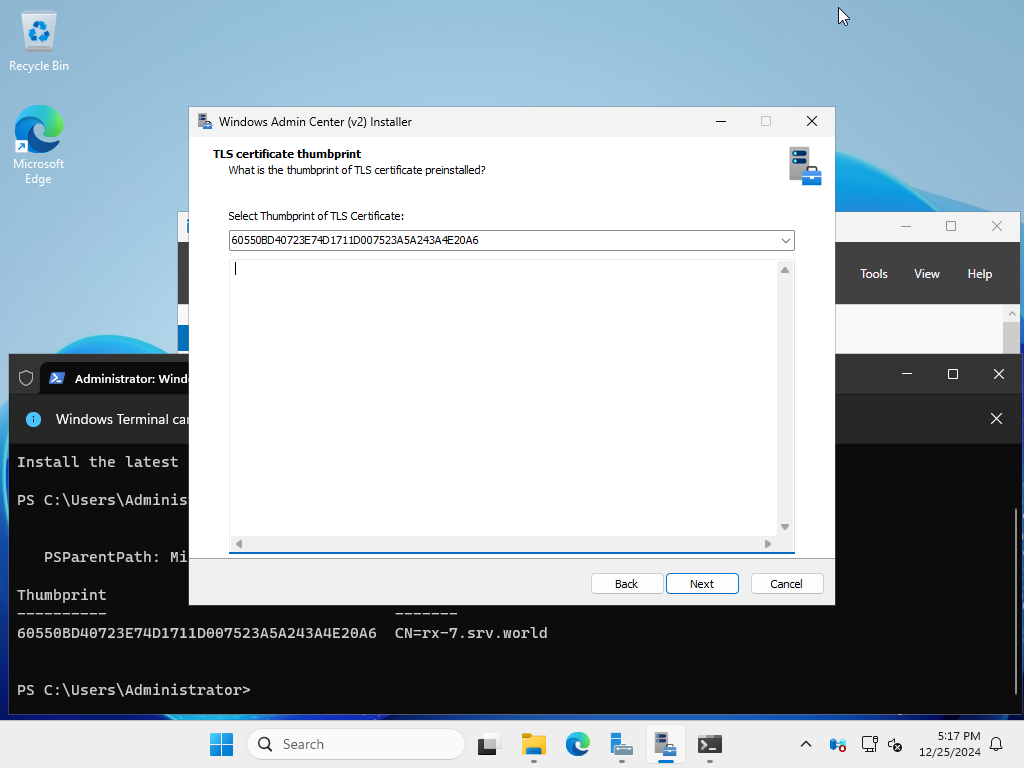
|
| [12] | If you have enabled remote access, specify the host name to be used for remote access as an FQDN (Fully Qualified Domain Name). This must match the DNS name set in the TLS certificate. |
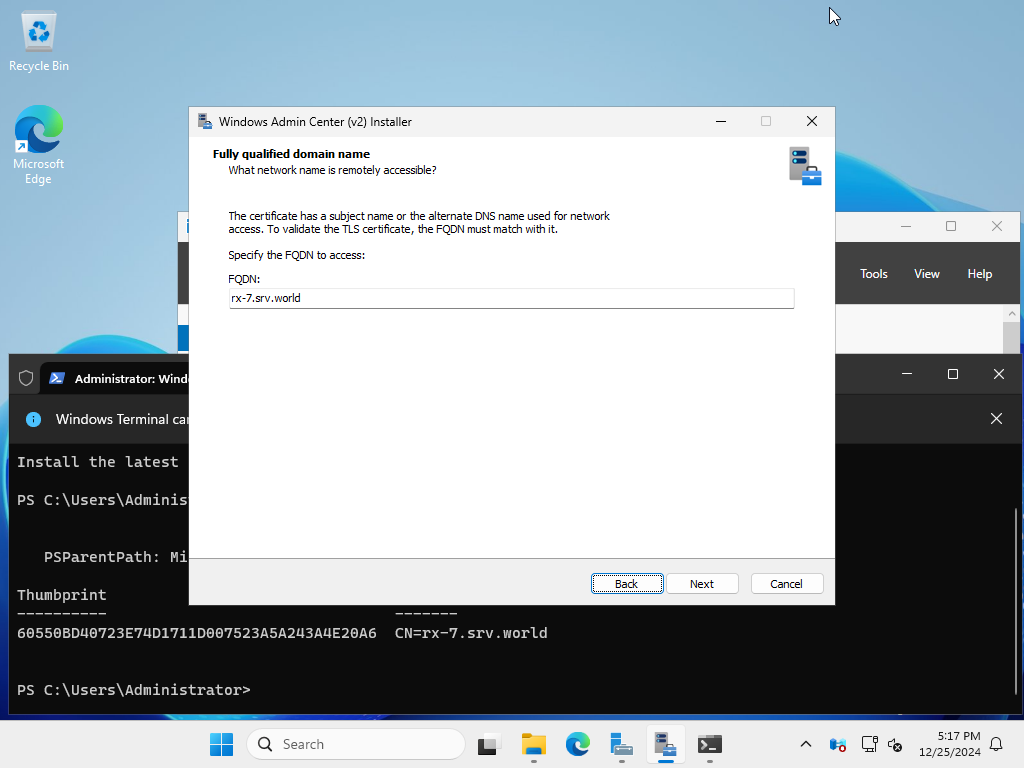
|
| [13] | If you allow remote access, select whether to limit access permissions to within the domain or to allow all. In this example, we will leave it at the default (allow all). |
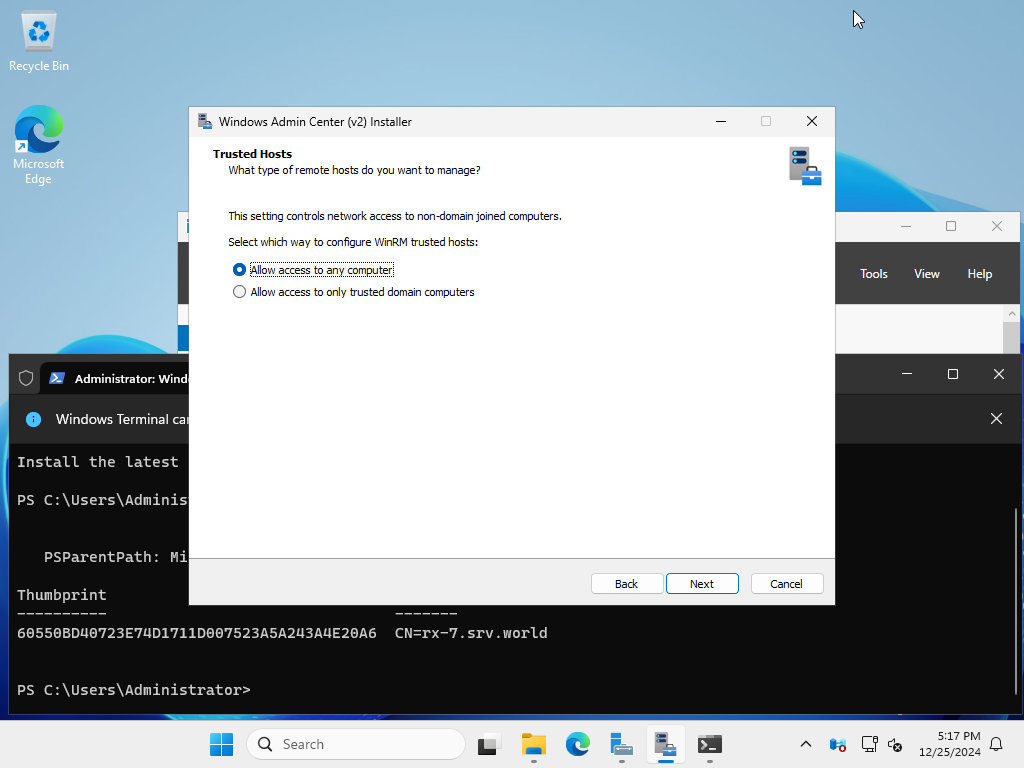
|
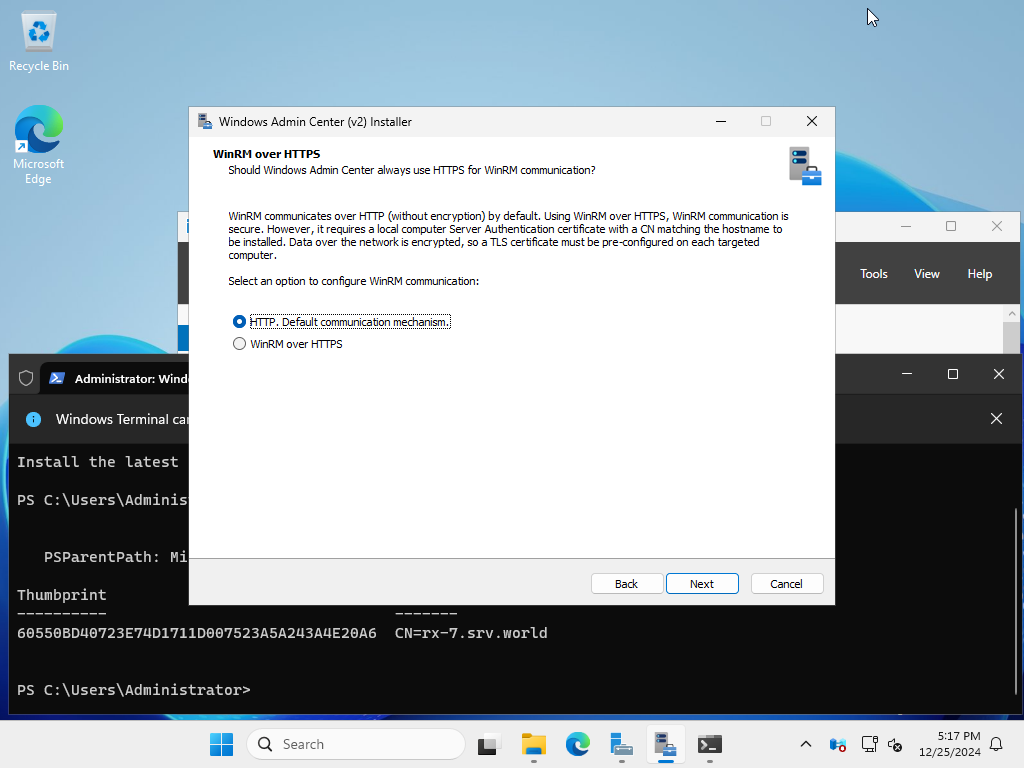
| [14] | When communicating with other hosts using WinRM, select whether to use HTTP or HTTPS. In this example, we will proceed with the default (HTTP). |
|
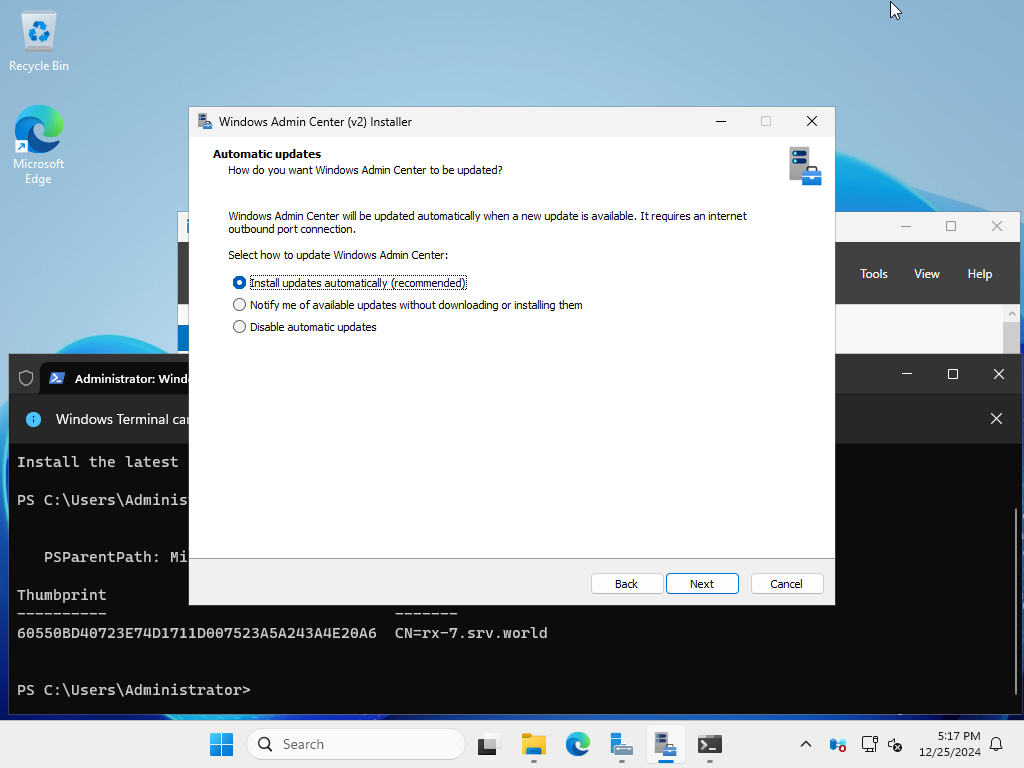
| [15] | Select the update method for Windows Admin Center. In this example, we will proceed with the default (automatic update). |
|
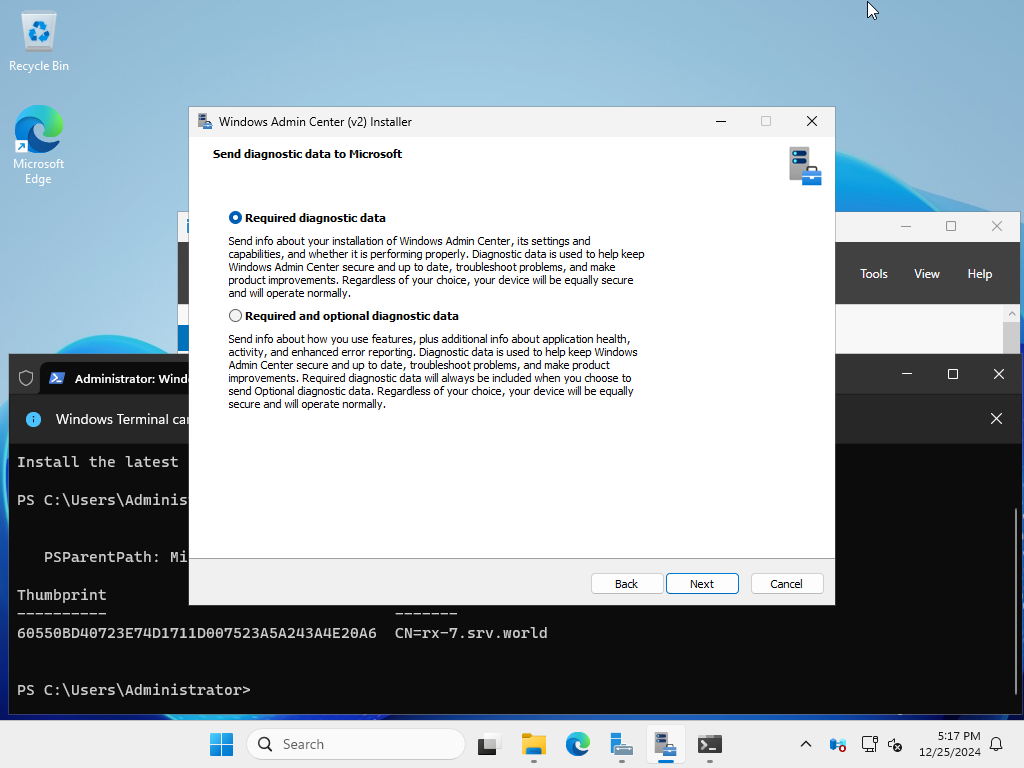
| [16] | Select the diagnostic data you want to send to Microsoft and proceed to the next step. In this example, we will proceed with the default (required diagnostic data). |
|
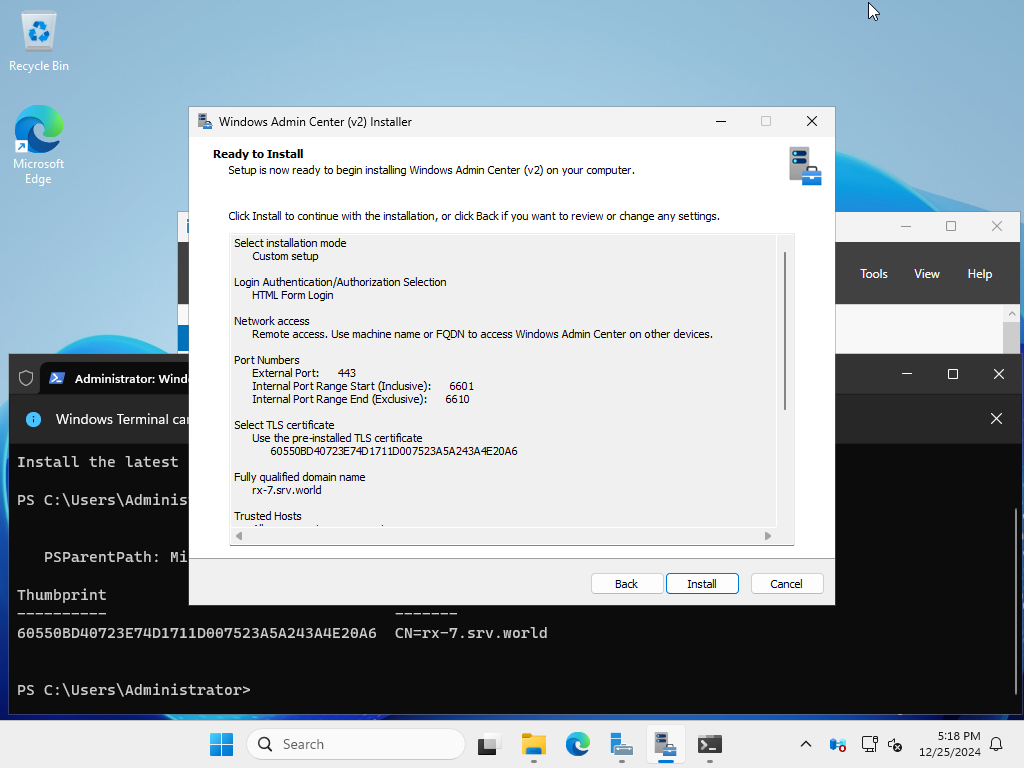
| [17] | Check the settings and click the [Install] button. |
|
| [18] | After the installation is complete, click the [Finish] button. |
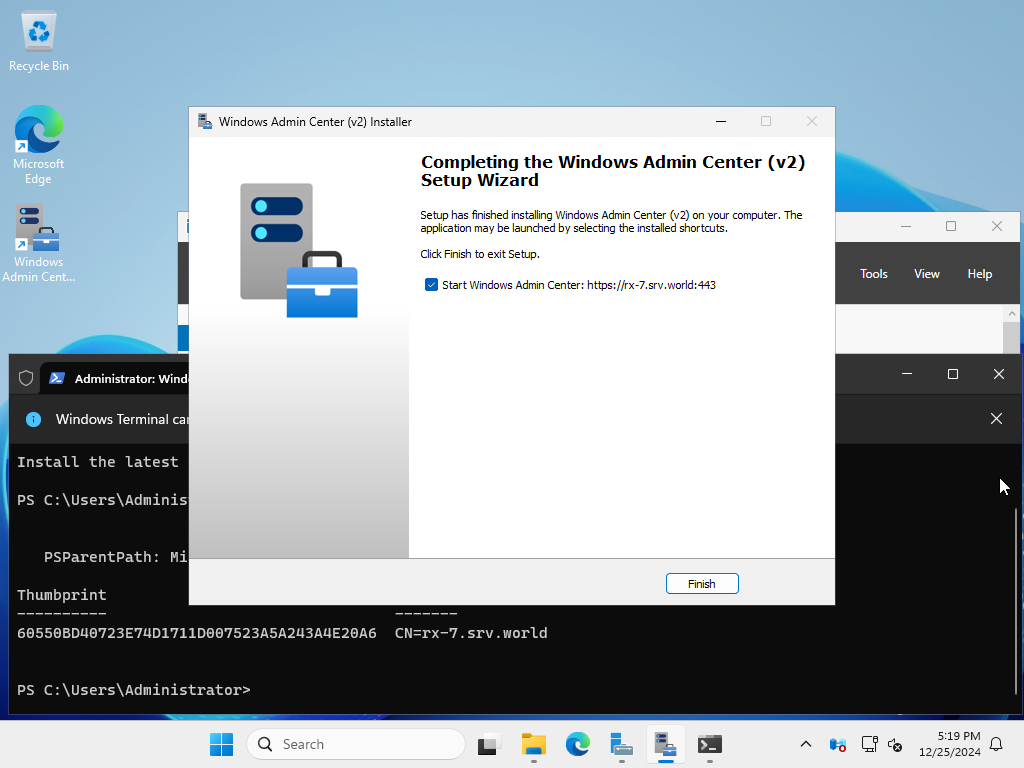
|
| [19] | If the web browser starts and the Windows Admin Center login screen is displayed correctly, the installation is complete. |
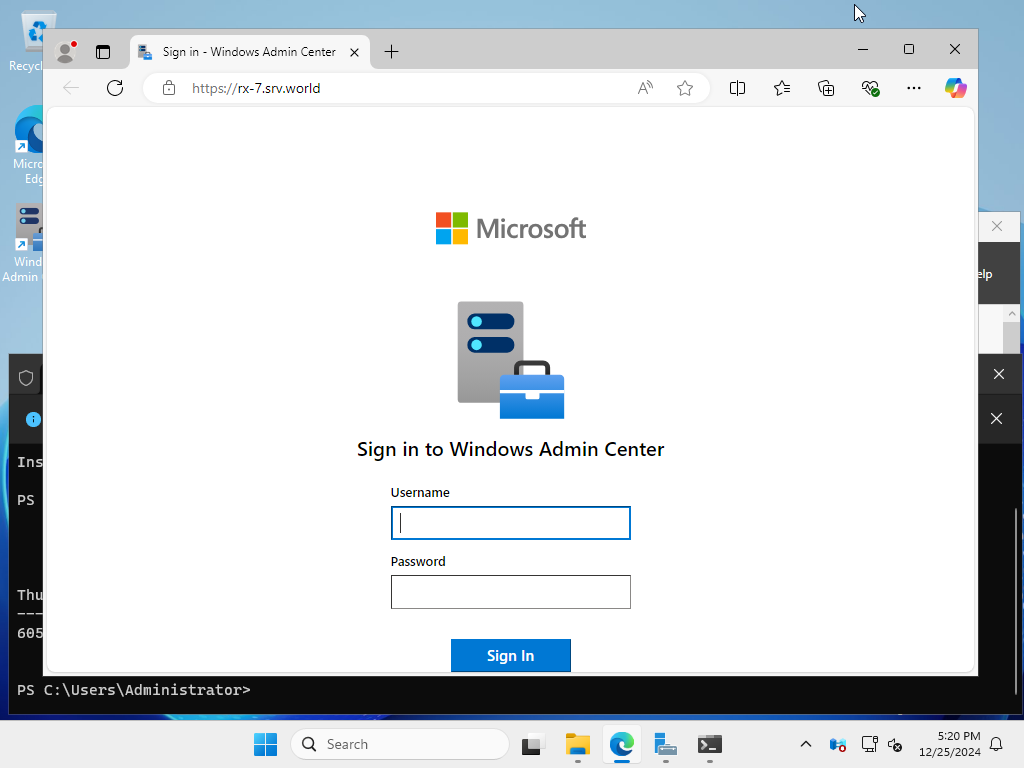
|