Kerberos Authentication2014/05/02 |
|
Enable Kerberos Authentication to limit access on specific web pages.
Users can authenticate with Windows Active Directory. It's necessarry to run Windows Active Directory in your LAN.
|
|
| [1] | For example, set Kerberos Authentication under the directory [/var/www/html/auth-kerberos]. |
|
root@www:~#
apt-get -y install libapache2-mod-auth-kerb # specify Realm name +------------------+ Configuring Kerberos Authentication +------------------+ | When users attempt to use Kerberos and specify a principal or user name | | without specifying what administrative Kerberos realm that principal | | belongs to, the system appends the default realm. The default realm may | | also be used as the realm of a Kerberos service running on the local | | machine. Often, the default realm is the uppercase version of the local | | DNS domain. | | | | Default Kerberos version 5 realm: | | | | FD3S.SRV.WORLD________________________________________________________ | | | | <Ok> | | | +---------------------------------------------------------------------------+ # specify Active Directory hostname +------------------+ Configuring Kerberos Authentication +------------------+ | Enter the hostnames of Kerberos servers in the FD3S.SRV.WORLD Kerberos | | realm separated by spaces. | | | | Kerberos servers for your realm: | | | | fd3s.srv.world________________________________________________________ | | | | <Ok> | | | +---------------------------------------------------------------------------+ # specify Active Directory hostname +------------------+ Configuring Kerberos Authentication +------------------+ | Enter the hostname of the administrative (password changing) server for | | the FD3S.SRV.WORLD Kerberos realm. | | | | Administrative server for your Kerberos realm: | | | | fd3s.srv.world________________________________________________________ | | | | <Ok> | | | +---------------------------------------------------------------------------+ # create keytab : HTTP/[AD's hostname or IP address]@[Realm name] root@www:~# echo "HTTP/fd3s.srv.world@FD3S.SRV.WORLD" > /etc/krb5.keytab
root@www:~#
vi /etc/apache2/sites-available/auth-kerberos.conf # create new
<Directory /var/www/html/auth-kerberos>
SSLRequireSSL
AuthType Kerberos
AuthName "Kerberos Authntication"
KrbAuthRealms FD3S.SRV.WORLD
Krb5Keytab /etc/krb5.keytab
KrbMethodNegotiate Off
KrbSaveCredentials Off
KrbVerifyKDC Off
Require valid-user
</Directory>
mkdir /var/www/html/auth-kerberos root@www:~# a2ensite auth-kerberos Enabling site auth-kerberos. To activate the new configuration, you need to run: service apache2 reloadroot@www:~# /etc/init.d/apache2 restart * Restarting web server apache2 ...done. # create a test page
root@www:~#
vi /var/www/html/auth-kerberos/index.html <html> <body> <div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;"> Test Page for Kerberos Auth </div> </body> </html> |
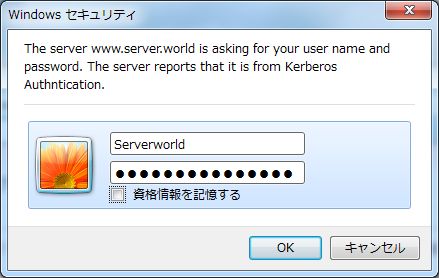
| [2] | Access to the test page with web browser, then authentication is required. Input user name on Active Directory and authenticate here. |
|
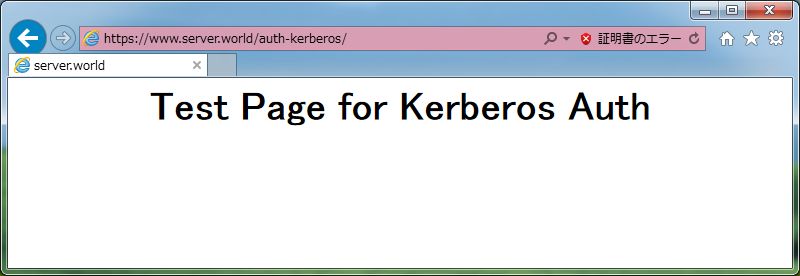
| [3] | Just accessed. |
|
Matched Content