File Server : SMB over QUIC2025/01/13 |
|
This is the setting for SMB over QUIC. Active Directory domain environment is not required, so this example will use a standalone file server. Also, since QUIC communicates on UDP 443, you will need to allow UDP 443 on the upstream router/firewall or configure port forwarding as necessary.
+----------------------+
| [ File Server ] |
| rx-7.srv.world |
| |
+-----------+----------+
|10.0.0.101
|
10.0.0.1|
+------+-----+
-------| Router |-------
+------+-----+
|
| Internet
--------------+-------------
|
|192.168.0.x
+-----------+----------+
| |
| Client PC |
| |
+----------------------+
|
| [1] | Run PowerShell with Admin Privilege and create a self-signed certificate for SMB over QUIC. If you use a valid certificate, you can skip creating a self-signed certificate. |
Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. # create a self-signed certificate PS C:\Users\Administrator> $ObjCert = New-SelfSignedCertificate ` -DnsName "rx-7.srv.world" ` -Subject "CN=SMB over QUIC" ` -KeyAlgorithm "ECDSA_nistP384" ` -KeyExportPolicy "Exportable" ` -CertStoreLocation "Cert:\LocalMachine\My" ` -NotAfter (Get-Date).AddYears(10) # export certificate for client computers PS C:\Users\Administrator> Export-Certificate -Cert $ObjCert -FilePath "C:\Users\Administrator\rx-7.srv.world.cer" Directory: C:\Users\Administrator Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 1/13/2025 11:49 AM 474 rx-7.srv.world.cer |
| [2] | Associate the certificate with the file server. |
Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. PS C:\Users\Administrator> Get-ChildItem Cert:\LocalMachine\My PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\My Thumbprint Subject ---------- ------- 02D01E6695C68E404BE00C53696F374EE25EAB7B CN=SMB over QUIC PS C:\Users\Administrator> New-SmbServerCertificateMapping -Name rx-7.srv.world ` -Thumbprint 02D01E6695C68E404BE00C53696F374EE25EAB7B ` -Store My Name Subject Thumbprint DisplayName StoreName Type Flags RequireClientAuthentication ---- ------- ---------- ----------- --------- ---- ----- ------------------- rx-7.srv.world CN=SMB over QUIC 02D01E6695C68E404BE00C53696F374EE25EAB7B SMB over QUIC My QUIC None False # with the above settings, it will listen on UDP/443 PS C:\Users\Administrator> netstat -a | Select-String 443 UDP 0.0.0.0:443 *:* UDP [::]:443 *:* # Firewall rules are predefined and the public profile is allowed but # the Domain and Private profiles must be enabled manually PS C:\Users\Administrator> Get-NetFirewallRule -DisplayName "File and Printer Sharing (SMB-QUIC-In)" Name : FPS-SMBQ-In-UDP DisplayName : File and Printer Sharing (SMB-QUIC-In) Description : Inbound rule for File and Printer Sharing to allow Server Message Block transmission and reception via Winquic. [UDP 443] DisplayGroup : File and Printer Sharing over QUIC Group : @FirewallAPI.dll,-28652 Enabled : False Profile : Domain, Private Platform : {} Direction : Inbound Action : Allow EdgeTraversalPolicy : Block LooseSourceMapping : False LocalOnlyMapping : True Owner : PrimaryStatus : OK Status : The rule was parsed successfully from the store. (65536) EnforcementStatus : NotApplicable PolicyStoreSource : PersistentStore PolicyStoreSourceType : Local RemoteDynamicKeywordAddresses : {} PolicyAppId : PackageFamilyName : Name : {C55B4291-6581-48A9-9140-CE42A285B1A2} DisplayName : File and Printer Sharing (SMB-QUIC-In) Description : Inbound rule for File and Printer Sharing to allow Server Message Block transmission and reception via Winquic. [UDP 443] DisplayGroup : File and Printer Sharing over QUIC Group : @FirewallAPI.dll,-28652 Enabled : True Profile : Public Platform : {} Direction : Inbound Action : Allow EdgeTraversalPolicy : Block LooseSourceMapping : False LocalOnlyMapping : True Owner : PrimaryStatus : OK Status : The rule was parsed successfully from the store. (65536) EnforcementStatus : NotApplicable PolicyStoreSource : PersistentStore PolicyStoreSourceType : Local RemoteDynamicKeywordAddresses : {} PolicyAppId : PackageFamilyName : |
| [3] | Transfer the exported certificate to the client computer that you want to access via SMB over QUIC, and import the certificate. |
Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. # transferred certificate PS C:\Users\Serverworld> Get-ChildItem rx-7.srv.world.cer Directory: C:\Users\Serverworld Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 1/13/2025 12:32 PM 474 rx-7.srv.world.cer PS C:\Users\Serverworld> Import-Certificate -FilePath C:\Users\Serverworld\rx-7.srv.world.cer -CertStoreLocation Cert:\LocalMachine\Root PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\Root Thumbprint Subject ---------- ------- 02D01E6695C68E404BE00C53696F374EE25EAB7B CN=SMB over QUIC |
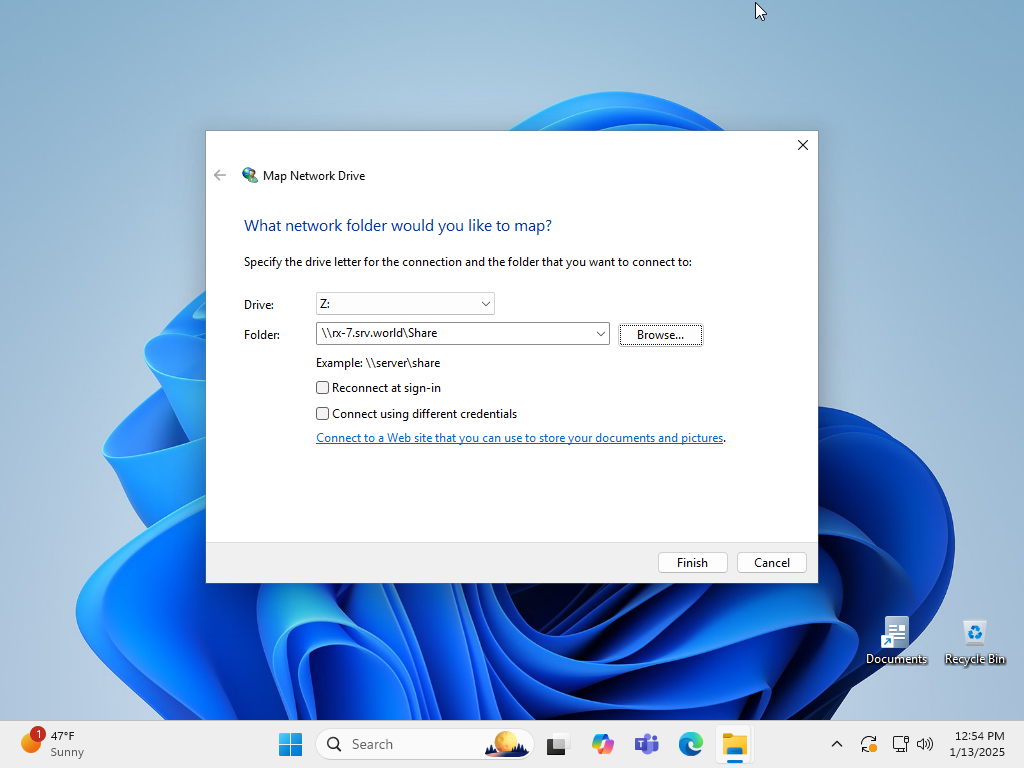
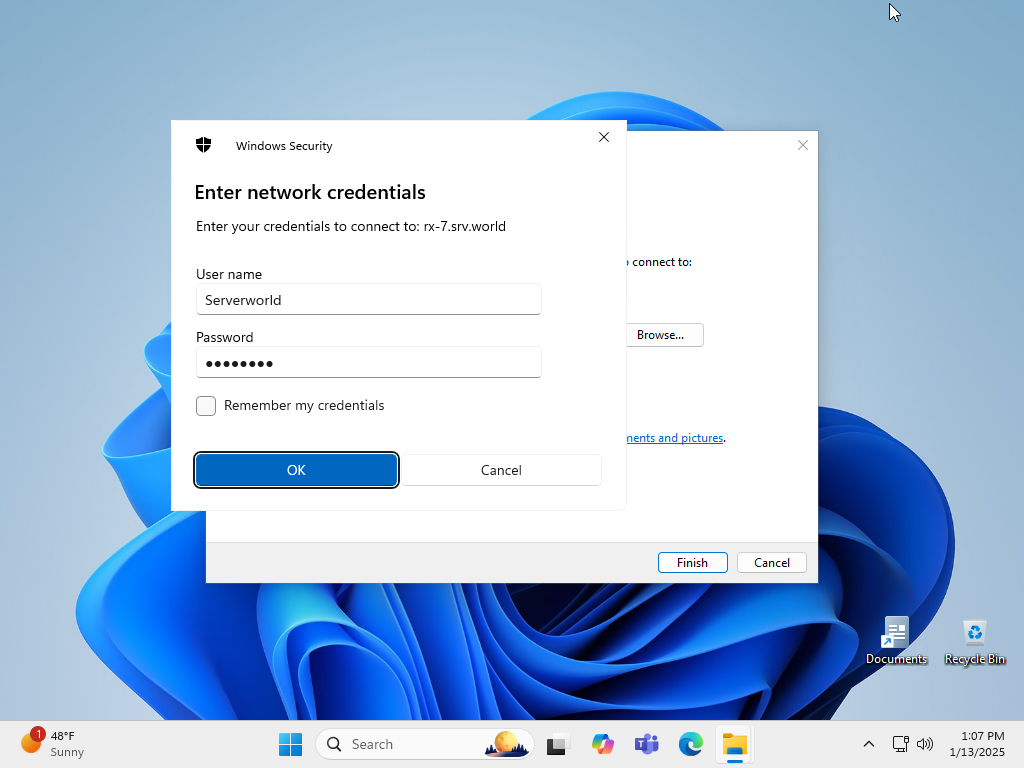
| [4] | Share access from client computers works as usual. Since a connection is made via 443/UDP after a connection via 445/TCP fails, it may take some time for the authentication form to appear. |
|
|
|
Matched Content