OpenSSH : SSH Key-Pair Authentication2024/10/31 |
|
Configure SSH server to login with Key-Pair Authentication.
Create a private key for client and a public key for server to do it. |
|
| [1] | Key pairs are created by each user, so the user who creates the key pair log in to any client computer and work as that user. |
|
# create key-pair [fedora@client ~]$ ssh-keygen Generating public/private ed25519 key pair. Enter file in which to save the key (/home/fedora/.ssh/id_ed25519): # Enter or input changes if you want Created directory '/home/fedora/.ssh'. Enter passphrase (empty for no passphrase): # set passphrase (if set no passphrase, Enter with empty) Enter same passphrase again: Your identification has been saved in /home/fedora/.ssh/id_ed25519 Your public key has been saved in /home/fedora/.ssh/id_ed25519.pub The key fingerprint is: SHA256:PMBZoNIrzv8y3ldJWzDGUS1D9pnmtL/khDYfC9PY67I fedora@client.srv.world The key's randomart image is: ..... .....[fedora@client ~]$ ll ~/.ssh total 8 -rw-------. 1 fedora fedora 464 Oct 31 11:25 id_ed25519 -rw-r--r--. 1 fedora fedora 105 Oct 31 11:25 id_ed25519.pub # copy the SSH public key you created to the server you want to log in to [fedora@client ~]$ ssh-copy-id dlp.srv.world
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/fedora/.ssh/id_ed25519.pub"
The authenticity of host 'dlp.srv.world (10.0.0.30)' can't be established.
ED25519 key fingerprint is SHA256:d6bbyQgjLbqg2eTAsxEgNeZX1b6w/3iotKQi54eFaOM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
fedora@dlp.srv.world's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'dlp.srv.world'"
and check to make sure that only the key(s) you wanted were added.
# verify whether you can log in to the server to which you copied the public key using key authentication [fedora@client ~]$ ssh dlp.srv.world hostname
Enter passphrase for key '/home/fedora/.ssh/id_ed25519': # if you set a passphrase, enter it
dlp.srv.world
|
| [2] | If you use key pair authentication, you can make your server more secure by disabling password authentication on the SSH server side as follows. |
|
[root@dlp ~]#
vi /etc/ssh/sshd_config # line 65, 69 : uncomment and change to [no] PasswordAuthentication no ..... ..... KbdInteractiveAuthentication no
systemctl restart sshd |
|
SSH Key-Pair Authentication on Windows Client #1
|
|
This is the example to login to SSH server from Windows Client.
It uses Putty on this example. Beforehand, transfer the SSH private key ([id_ed25519] in the above example) to the Windows client. |
|
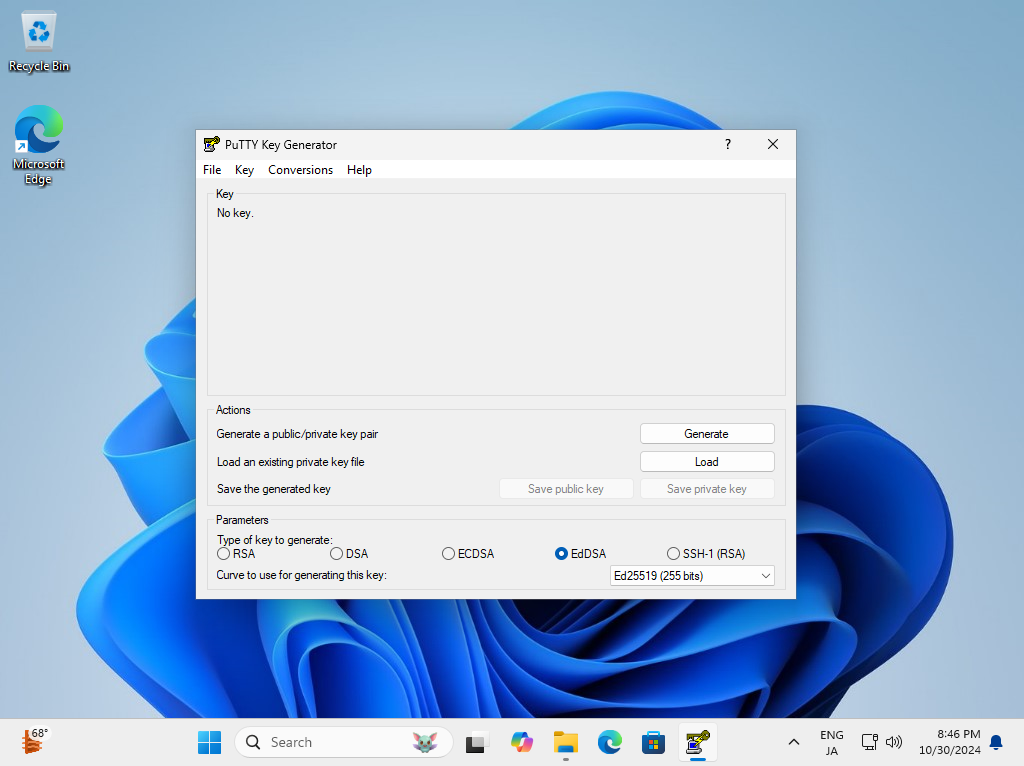
| [3] | Run [Puttygen.exe] that is included in [Putty]. (placed in the folder [Putty.exe] is also placed) If not included, Download it from official site (www.chiark.greenend.org.uk/~sgtatham/putty/). After starting [Puttygen.exe], Click [Load] button on the following window. |
|
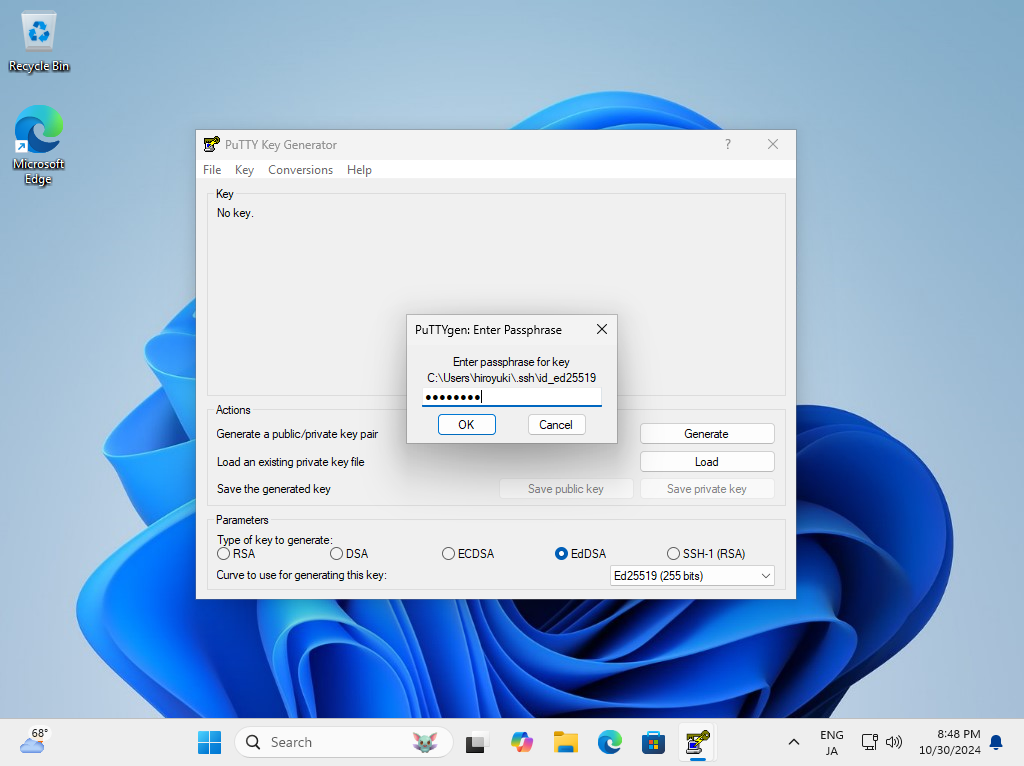
| [4] | Specify the private key that you transferred from SSH server, then passphrase is required like follows, answer it. (if not set passphrase, this step is skipped) |
|
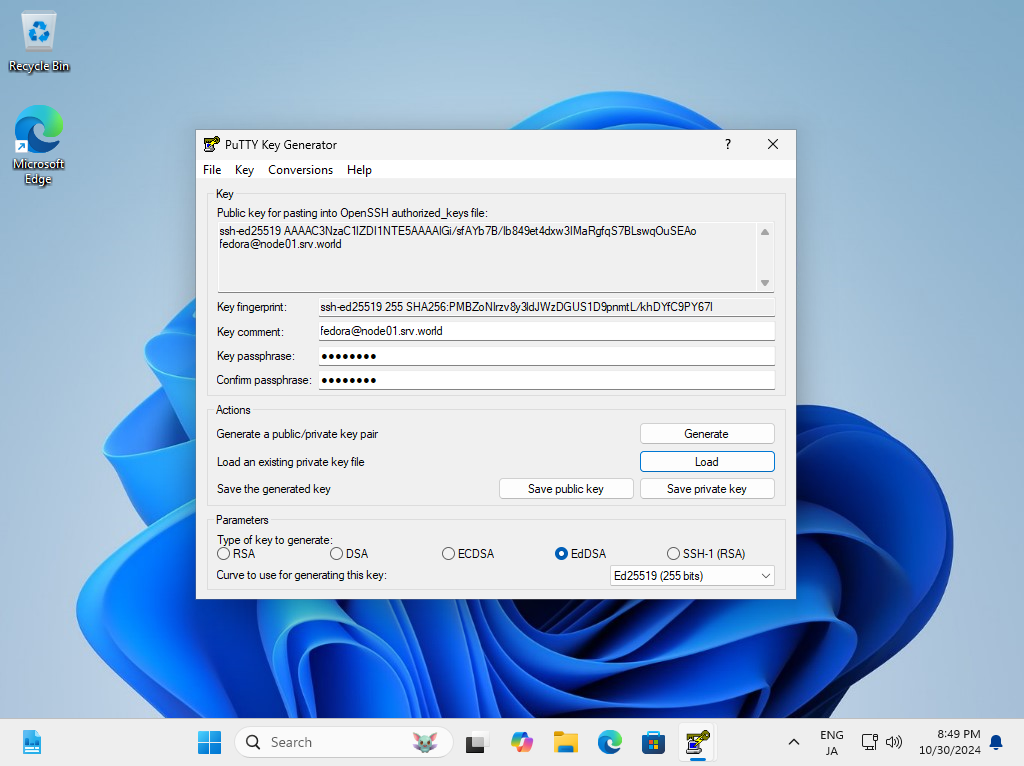
| [5] | Click [Save private key] button to save it under a folder you like with any file name you like. |
|
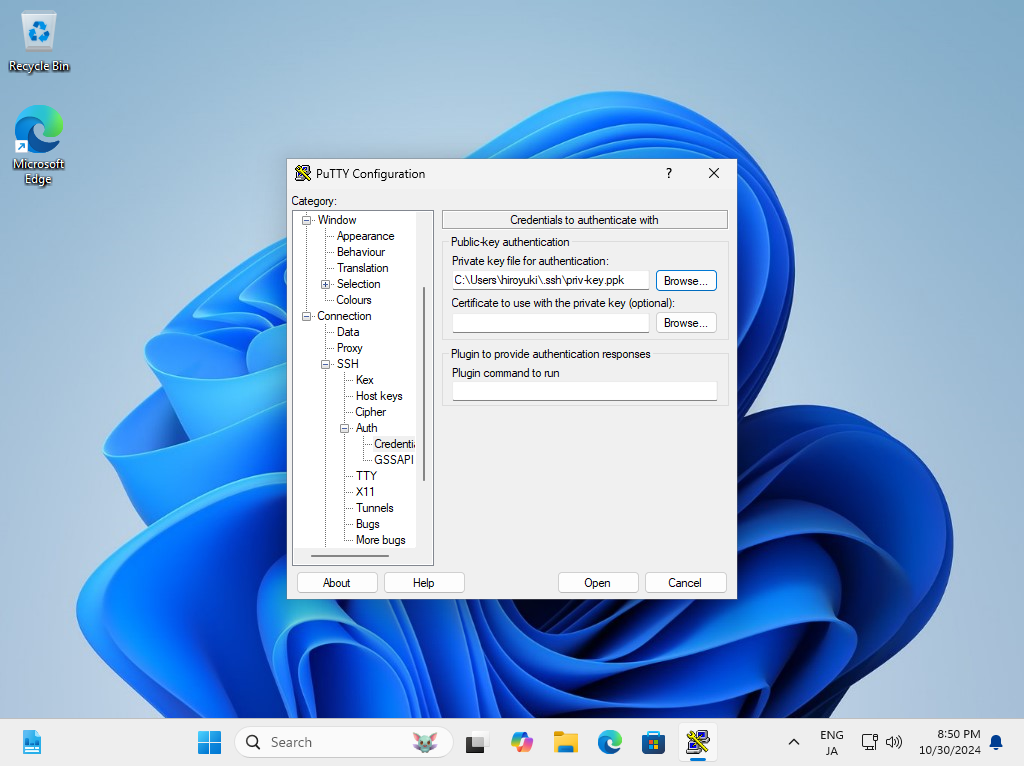
| [6] | Start Putty and Open [Connection] - [SSH] - [Auth] - [Credentials] on the left pane, then specify your private key on the [Private key file] field. |
|
| [7] | Back to the [Session] on the left pane and specify your SSH server host to Connect. |
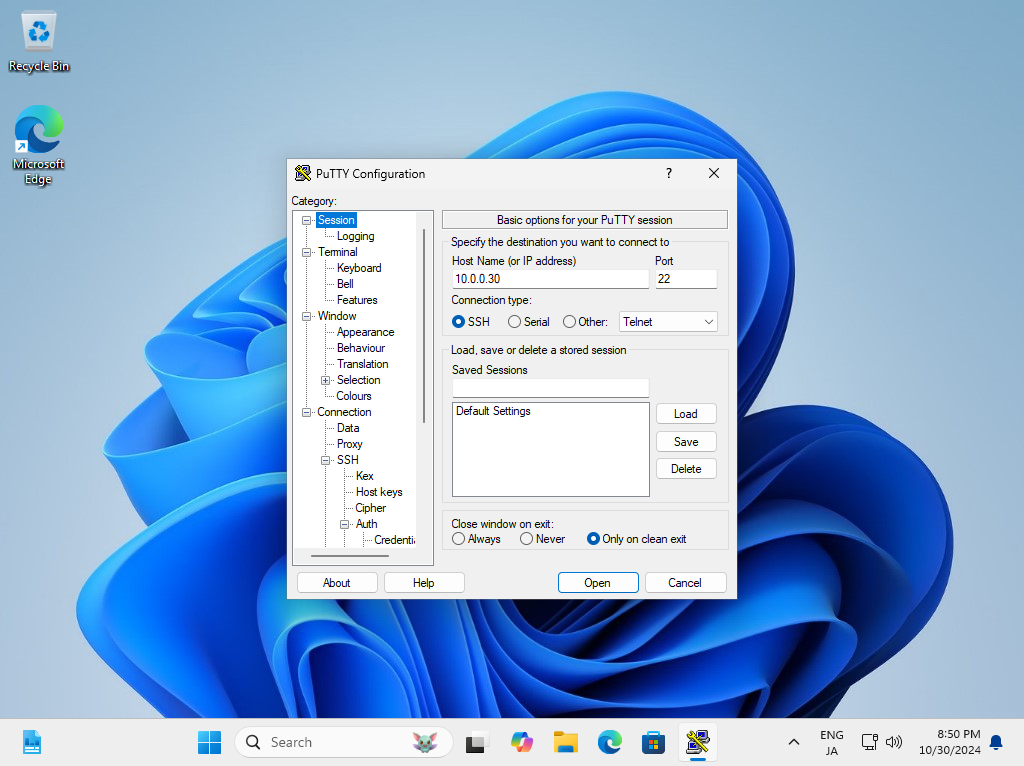
|
| [8] | When SSH key-pair is set, the passphrase if it is set is required to login like follows, then answer it. |
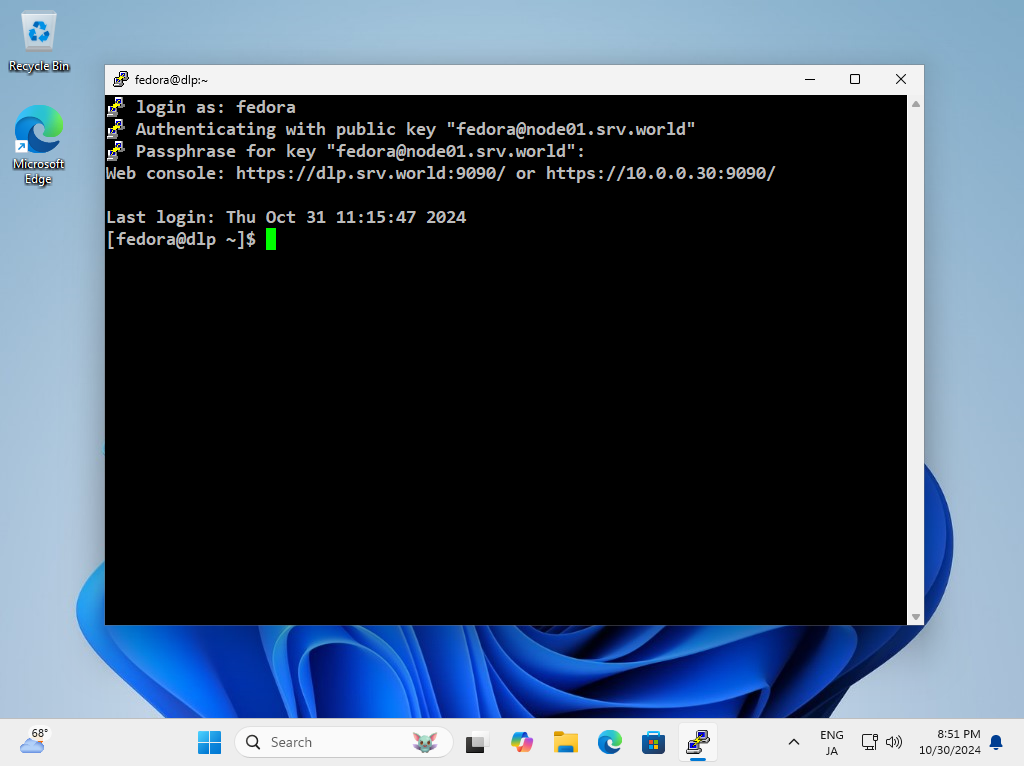
|
|
SSH Key-Pair Authentication on Windows #2
|
| [9] | On Windows 11, OpenSSH Client has been implemented as a Windows feature, so it's possible to authenticate with SSH Key-Pair without Putty and other 3rd party softwares. Transfer your private key to your Windows 11 and put it under the [(logon user home).ssh] folder like follows, then it's ready to use Key-Pair authentication. |
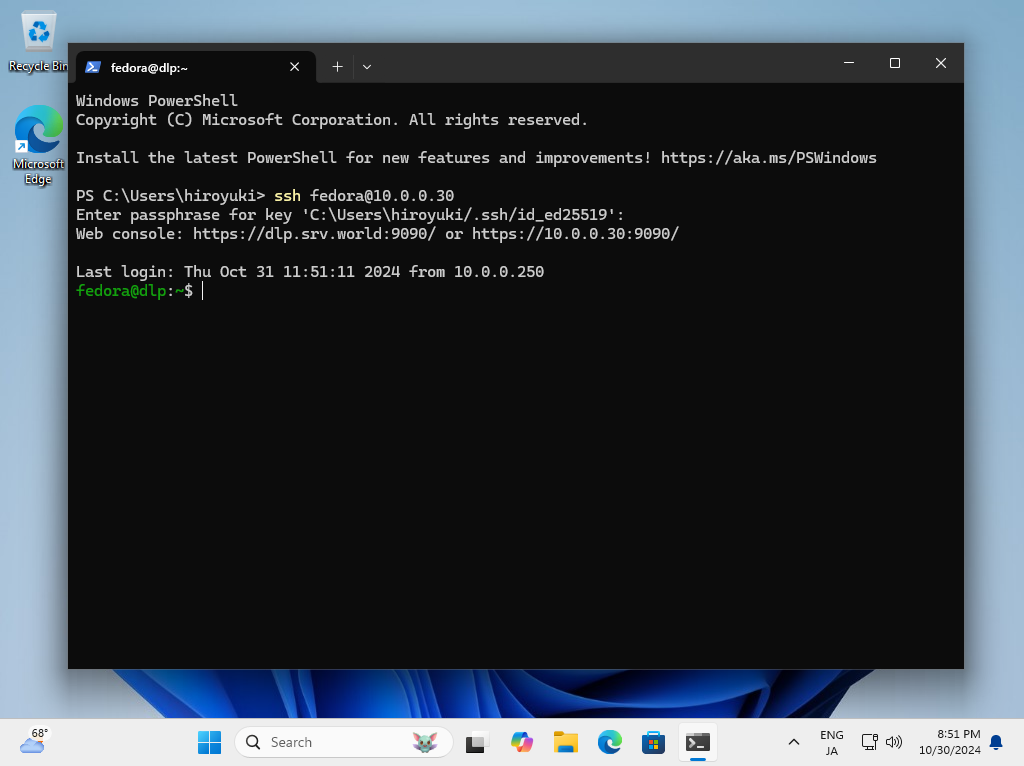
|
Matched Content