Nginx : Basic Authentication + Kerberos2023/07/04 |
|
Configure Nginx to use Windows Active Directory users on Basic authentication.
Windows Active Directory is required in your local network, refer to here.
This example is based on the environment like follows.
|
|||||||||||
| [1] |
Username and password are sent with plain text on Basic Authentication,
so Use secure connection with SSL/TLS setting, refer to here. |
||||||||||
| [2] | Install packages which includes [mod-http-auth-pam] module. |
|
root@www:~#
apt -y install nginx-extras libpam-krb5 # specify Realm +------------------+ Configuring Kerberos Authentication +------------------+ | When users attempt to use Kerberos and specify a principal or user name | | without specifying what administrative Kerberos realm that principal | | belongs to, the system appends the default realm. The default realm may | | also be used as the realm of a Kerberos service running on the local | | machine. Often, the default realm is the uppercase version of the local | | DNS domain. | | | | Default Kerberos version 5 realm: | | | | SRV.WORLD________________________________________________________________ | | | | <Ok> | | | +---------------------------------------------------------------------------+ # specify Active Directory's hostname +------------------+ Configuring Kerberos Authentication +------------------+ | Enter the hostnames of Kerberos servers in the FD3S.SRV.WORLD Kerberos | | realm separated by spaces. | | | | Kerberos servers for your realm: | | | | fd3s.srv.world___________________________________________________________ | | | | <Ok> | | | +---------------------------------------------------------------------------+ # specify Active Directory's hostname +------------------+ Configuring Kerberos Authentication +------------------+ | Enter the hostname of the administrative (password changing) server for | | the FD3S.SRV.WORLD Kerberos realm. | | | | Administrative server for your Kerberos realm: | | | | fd3s.srv.world___________________________________________________________ | | | | <Ok> | | | +---------------------------------------------------------------------------+ |
| [3] | Configure Basic authentication + Kerberos. For example, set Basic Authentication to the directory [/var/www/html/auth-kerberos]. |
|
root@www:~#
vi /etc/nginx/sites-available/default # add settings into [server] section in a virtualhost you'd like to set
server {
listen 443 ssl http2 default_server;
listen [::]:443 ssl http2 default_server;
server_name www.srv.world;
root /var/www/html;
ssl_certificate "/etc/letsencrypt/live/www.srv.world/fullchain.pem";
ssl_certificate_key "/etc/letsencrypt/live/www.srv.world/privkey.pem";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
index index.html
include /etc/nginx/default.d/*.conf;
location / {
try_files $uri $uri/ =404;
}
location /auth-kerberos {
auth_pam "Kerberos Authentication";
auth_pam_service_name "nginx-krb5";
}
.....
.....
root@www:~#
vi /etc/pam.d/nginx-krb5 # create new auth sufficient pam_krb5.so use_first_pass account sufficient pam_krb5.so
root@www:~#
systemctl reload nginx # create a test page root@www:~# mkdir /var/www/html/auth-kerberos root@www:~# vi /var/www/html/auth-kerberos/index.html <html> <body> <div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;"> Test Page for Kerberos Auth </div> </body> </html> |
| [4] | Access to the test page from any client computer with web browser. Then authentication is required as settings, answer with any AD user. |
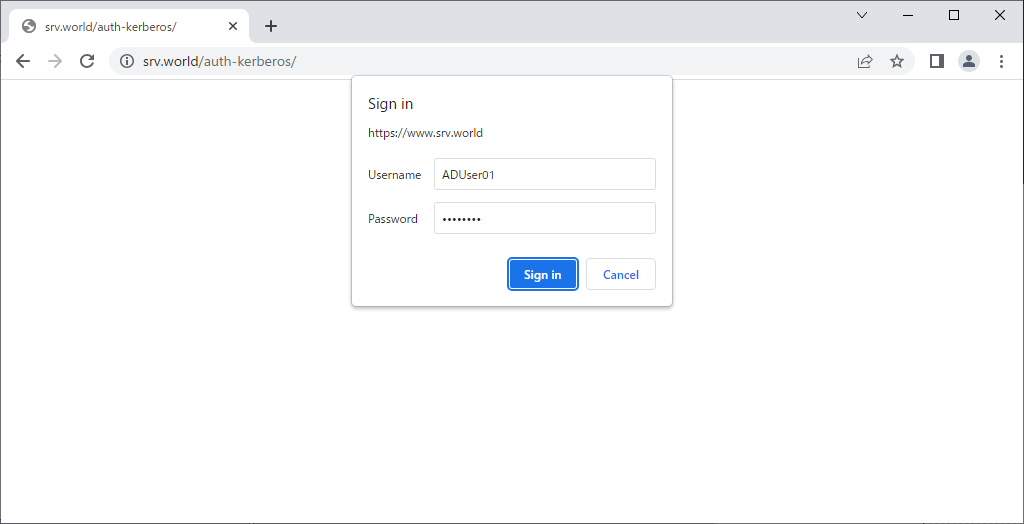
|
| [5] | That's OK if authentication is successfully passed and test page is displayed normally. |

|
Matched Content