FreeIPA : FreeIPA trust AD2021/08/04 |
|
FreeIPA ドメインと Windows Active Directory ドメイン間で信頼関係を構築する クロス フォレスト トラスト の設定です。
Windows Active Directory ドメインのユーザーアカウントで FreeIPA ドメインのリソースにアクセスできるようになります。 当例では以下のような環境を例にします。
+----------------------+ | +----------------------+ | [ FreeIPA (Rocky) ] |10.0.0.40 | 10.0.0.100| [ AD (Win 2019) ] | | dlp.ipa.srv.world +----------+-----------+ fd3s.ad.srv.world | | | | | +----------------------+ +----------------------+ |
| [1] | 構築済みの FreeIPA サーバー上で FreeIPA trust AD をインストールします。 |
|
[root@dlp ~]#
[root@dlp ~]# dnf module -y install idm:DL1/adtrust ipa-adtrust-install The log file for this installation can be found in /var/log/ipaserver-install.log ============================================================================== This program will setup components needed to establish trust to AD domains for the IPA Server. This includes: * Configure Samba * Add trust related objects to IPA LDAP server To accept the default shown in brackets, press the Enter key. Configuring cross-realm trusts for IPA server requires password for user 'admin'. This user is a regular system account used for IPA server administration. # FreeIPA admin パスワードで応答 admin password: WARNING: The smb.conf already exists. Running ipa-adtrust-install will break your existing samba configuration. # smb.conf を上書きしてよいかの確認 Do you wish to continue? [no]: yes Do you want to enable support for trusted domains in Schema Compatibility plugin? This will allow clients older than SSSD 1.9 and non-Linux clients to work with trusted users. # slapi-nis を有効にするか否か # SSSD 1.9 以前の古い Linux OS などとの互換性 Enable trusted domains support in slapi-nis? [no]: Trust is configured but no NetBIOS domain name found, setting it now. Enter the NetBIOS name for the IPA domain. Only up to 15 uppercase ASCII letters, digits and dashes are allowed. Example: EXAMPLE. # FreeIPA ドメインの NetBIOS 名を設定 NetBIOS domain name [IPA]: IPA01 WARNING: 9 existing users or groups do not have a SID identifier assigned. Installer can run a task to have ipa-sidgen Directory Server plugin generate the SID identifier for all these users. Please note, in case of a high number of users and groups, the operation might lead to high replication traffic and performance degradation. Refer to ipa-adtrust-install(1) man page for details. # 既存ユーザー向けに SID を作成するタスクを実行するか否か Do you want to run the ipa-sidgen task? [no]: yes The following operations may take some minutes to complete. Please wait until the prompt is returned. Configuring CIFS [1/24]: validate server hostname [2/24]: stopping smbd [3/24]: creating samba domain object ..... ..... [22/24]: starting CIFS services [23/24]: adding SIDs to existing users and groups This step may take considerable amount of time, please wait.. [24/24]: restarting smbd Done configuring CIFS. ============================================================================= Setup complete You must make sure these network ports are open: TCP Ports: * 135: epmap * 138: netbios-dgm * 139: netbios-ssn * 445: microsoft-ds * 1024..1300: epmap listener range * 3268: msft-gc UDP Ports: * 138: netbios-dgm * 139: netbios-ssn * 389: (C)LDAP * 445: microsoft-ds See the ipa-adtrust-install(1) man page for more details ============================================================================= # firewalld 稼働中の場合は以下も設定 [root@dlp ~]# firewall-cmd --add-service=freeipa-trust success [root@dlp ~]# firewall-cmd --runtime-to-permanent success |
| [2] | FreeIPA サーバー上で DNS 関連の設定を追加します。 |
|
# ipa dnsforwardzone-add [ADのドメイン名] --forwarder=[ADのIPアドレス] --forward-policy=only [root@dlp ~]# ipa dnsforwardzone-add ad.srv.world --forwarder=10.0.0.100 --forward-policy=only Server will check DNS forwarder(s). This may take some time, please wait ... Zone name: ad.srv.world. Active zone: TRUE Zone forwarders: 10.0.0.100 Forward policy: only # ipa dnszone-mod [IPAのドメイン名] --allow-transfer=[ADのIPアドレス] [root@dlp ~]# ipa dnszone-mod ipa.srv.world --allow-transfer=10.0.0.100 Zone name: ipa.srv.world. Active zone: TRUE Authoritative nameserver: dlp.ipa.srv.world. Administrator e-mail address: hostmaster.ipa.srv.world. SOA serial: 1628052219 SOA refresh: 3600 SOA retry: 900 SOA expire: 1209600 SOA minimum: 3600 BIND update policy: grant IPA.SRV.WORLD krb5-self * A; grant IPA.SRV.WORLD krb5-self * AAAA; grant IPA.SRV.WORLD krb5-self * SSHFP; Dynamic update: TRUE Allow query: any; Allow transfer: 10.0.0.100; |
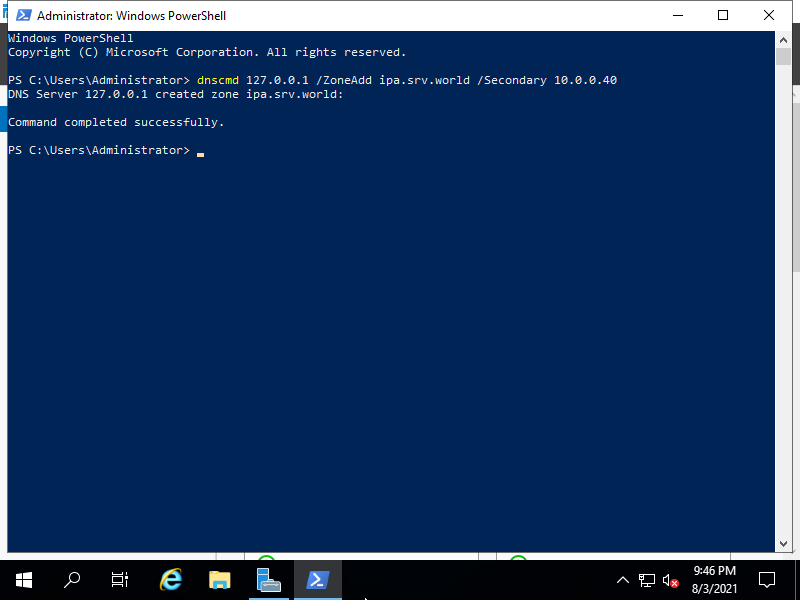
| [3] | Windows Active Directory 側でも FreeIPA ドメインをゾーンに追加します。 ⇒ dnscmd 127.0.0.1 /ZoneAdd [IPAのドメイン名] /Secondary [IPAのIPアドレス] |
|
| [4] | 名前解決の確認をした後、問題なければ FreeIPA trust AD をセットアップします。 |
|
[root@dlp ~]# dig SRV _ldap._tcp.ipa.srv.world ; <<>> DiG 9.11.26-RedHat-9.11.26-4.el8_4 <<>> SRV _ldap._tcp.ipa.srv.world ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 41569 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 3 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: 2158938e077790ca8a8a1af2610a1bac0cc7f28b7b694c83 (good) ;; QUESTION SECTION: ;_ldap._tcp.ipa.srv.world. IN SRV ;; ANSWER SECTION: _ldap._tcp.ipa.srv.world. 86400 IN SRV 0 100 389 node01.ipa.srv.world. _ldap._tcp.ipa.srv.world. 86400 IN SRV 0 100 389 dlp.ipa.srv.world. ;; AUTHORITY SECTION: ipa.srv.world. 86400 IN NS node01.ipa.srv.world. ipa.srv.world. 86400 IN NS dlp.ipa.srv.world. ;; ADDITIONAL SECTION: dlp.ipa.srv.world. 1200 IN A 10.0.0.40 node01.ipa.srv.world. 1200 IN A 10.0.0.61 ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Wed Aug 04 13:46:36 JST 2021 ;; MSG SIZE rcvd: 218[root@dlp ~]# dig SRV _ldap._tcp.ad.srv.world ; <<>> DiG 9.11.26-RedHat-9.11.26-4.el8_4 <<>> SRV _ldap._tcp.ad.srv.world ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 50823 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 4, ADDITIONAL: 9 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: 067fbb06b5d59df9cc054733610a1bdc94317c8d81cb64c4 (good) ;; QUESTION SECTION: ;_ldap._tcp.ad.srv.world. IN SRV ;; ANSWER SECTION: _ldap._tcp.ad.srv.world. 600 IN SRV 0 100 389 fd3s.ad.srv.world. ..... ..... # ipa trust-add --type=ad [ADのドメイン名] --admin Administrator --password [root@dlp ~]# ipa trust-add --two-way=true --type=ad ad.srv.world --admin Administrator --password Active Directory domain administrator's password: ----------------------------------------------------- Added Active Directory trust for realm "ad.srv.world" ----------------------------------------------------- Realm name: ad.srv.world Domain NetBIOS name: FD3S01 Domain Security Identifier: S-1-5-21-661807063-3256906606-4132121449 Trust direction: Two-way trust Trust type: Active Directory domain Trust status: Established and verified # 任意の AD ユーザーの情報が取得できるか確認 [root@dlp ~]# id Serverworld@ad.srv.world uid=466801103(serverworld@ad.srv.world) gid=466801103(serverworld@ad.srv.world) groups=466801103(serverworld@ad.srv.world),466800513(domain users@ad.srv.world) # 必要があれば有効に設定 (初回ログイン時にホームディレクトリを自動生成) [root@dlp ~]# authselect enable-feature with-mkhomedir [root@dlp ~]# systemctl enable --now oddjobd
# 任意の AD ユーザーでログイン可能か確認 [root@dlp ~]# exit logout Rocky Linux 8.4 (Green Obsidian) Kernel 4.18.0-305.7.1.el8_4.x86_64 on an x86_64 Activate the web console with: systemctl enable --now cockpit.socket dlp login: Serverworld@ad.srv.world Password: [serverworld@ad.srv.world@dlp ~]$ # ログインできた |
関連コンテンツ